Confidential Computing
Confidential Computing

R3 Product Vision

A New R3 Developer Experience, Tools and Community (AA)

Trust Technology Tackling Human Trafficking

Trust Technology: From Digital First to Digital Trust with DLT
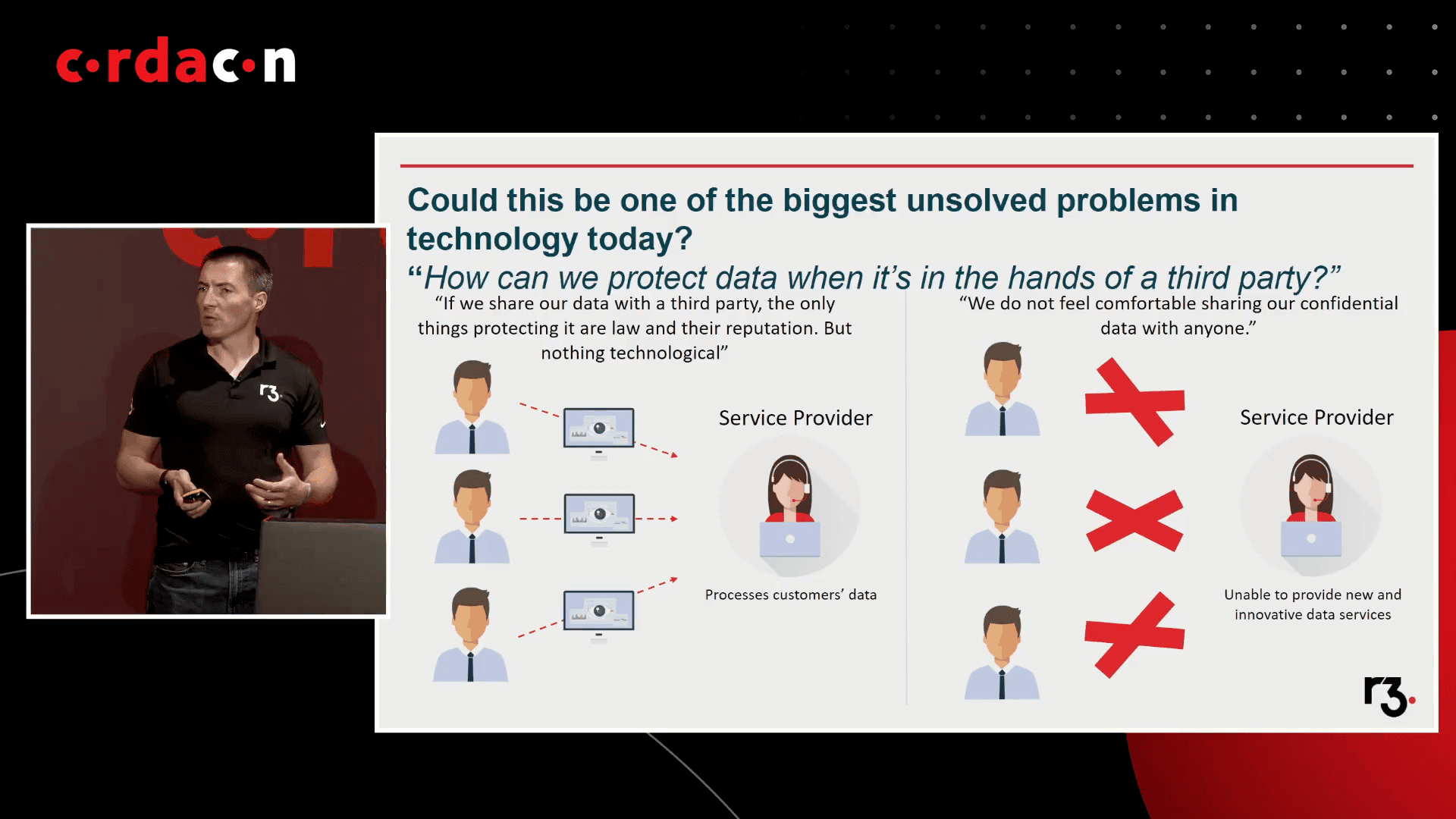
The Future of Data Privacy and Data Misuse

R3 Keynote and Welcome
